SentryBox has been discontinued. Thank you for being part of the journey — learn more in our blog post
Imagine a world where detecting hackers in your network is as simple as plugging in a
device—no complicated setup, no ongoing maintenance, just seamless protection. That’s the vision behind
SentryBox, a plug-and-play security solution designed to keep businesses safe with minimal
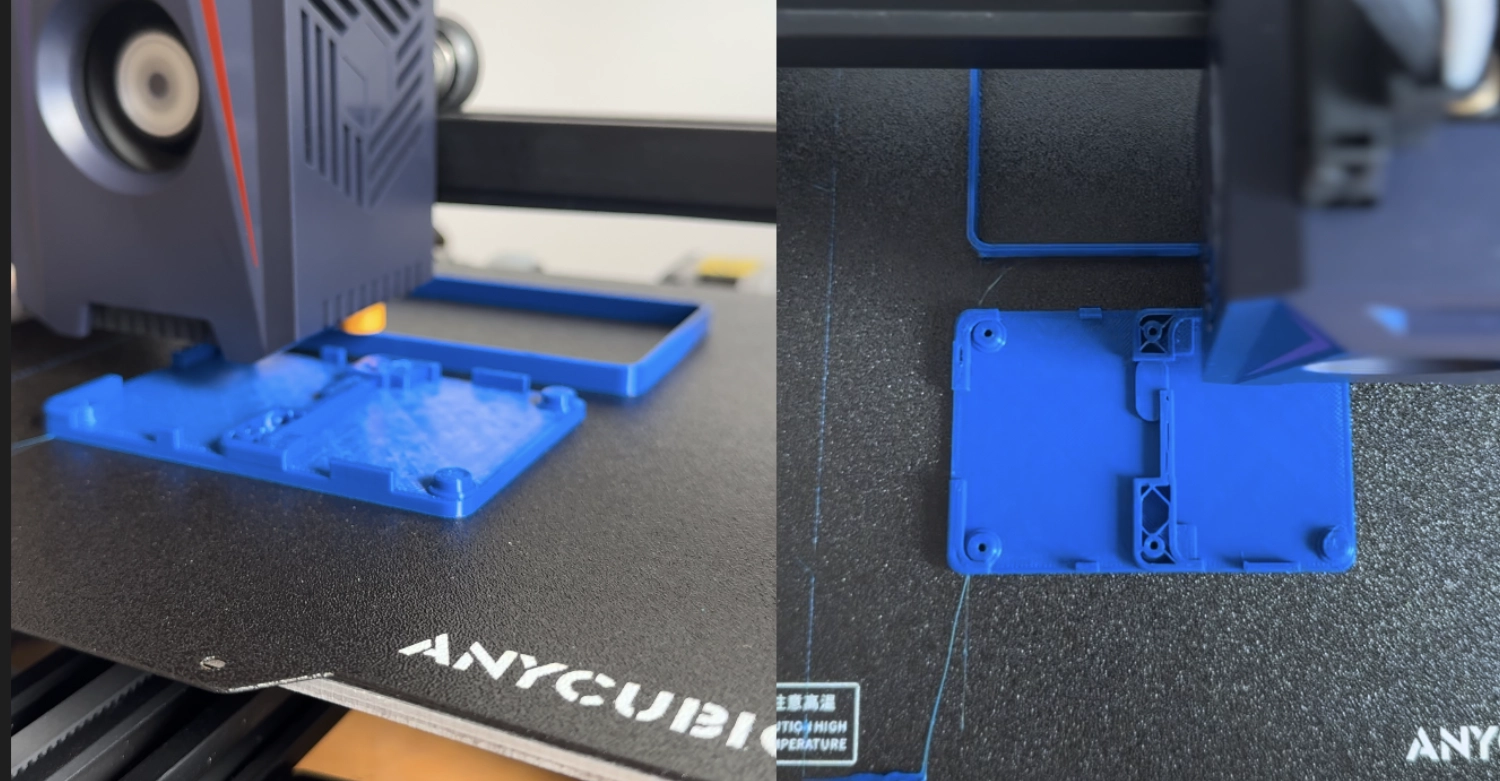
effort. From robust hardware choices to sleek 3D-printed prototypes, we’re refining every detail to create a
professional-grade device that blends security with simplicity. Read on to discover how we’re bringing this
innovation to life!

Coming up with an idea and transforming it into a finished product is always a long
journey. First, we'll develop a plug-and-play device that mimics actual network devices, starting with the
software. With Ubuntu Server running the show, our device will feature a Device Manager for maintenance and a
HoneyPot Service to lure and trap hackers.
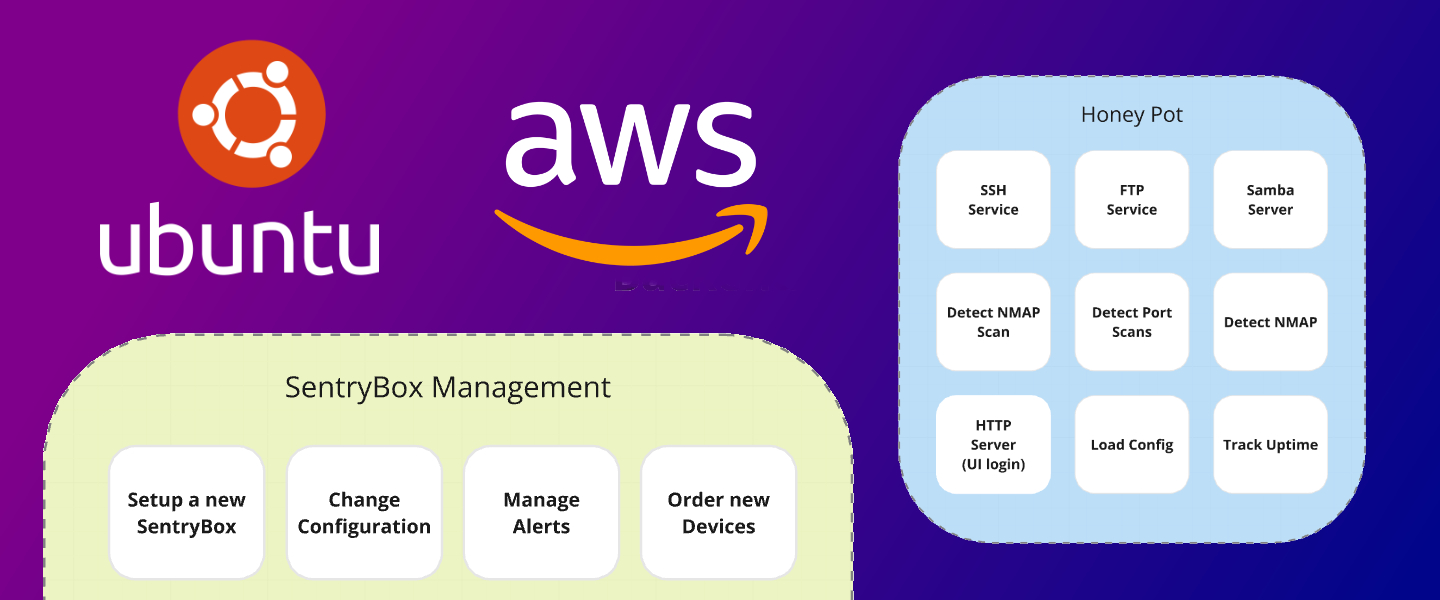
Coming up with an idea and transforming it into a finished product is always a long
journey. First, we'll develop a plug-and-play device that mimics actual network devices, starting with the
software. With Ubuntu Server running the show, our device will feature a Device Manager for maintenance and a
HoneyPot Service to lure and trap hackers.

Three years ago, I left WunderFleet, a company I founded and build with passion and a
focus on security. We managed millions of customers' personal information and facilitated 20 million vehicle
bookings annually, prioritizing cloud security with top-notch practices.
Despite our strong cloud
defenses, our local network was vulnerable, susceptible to simple phishing attacks.Exploring cybersecurity
solutions revealed a common issue: they required complex setups and custom sales, lacking the immediate
visibility we needed. This is our journey through the cybersecurity landscape, seeking an efficient, on-demand
solution...